6 Microsoft Teams features Zoom doesn’t have
One of the major news in March 2016 was that Microsoft was considering bidding $8 billion to purchase Slack. However, Bill Gates and the team decided that instead of buying Slack, they would develop their own chat app tool. Teams is mostly a Slack alternative, but it’s also meant to replace Skype for Business, which up until recently was Microsoft’s corporate video conferencing service. The app’s main functionality is the group chat that comes with plenty of features. Some of these features include editing, deleting, pinning messages, as well as starting a new thread and sharing files. You can even send .gif images, as well as emojis. Possibly due to Skype’s legacy, Teams includes a bunch of video features that Zoom doesn’t. There are real-time captions, built-in meeting notes, and a bizarre feature where you can pretend you’re in the same room as your coworkers!
To be clear: Zoom is a perfectly capable and liked solution. That doesn’t mean other apps are not offering anything interesting, and Microsoft in particular is trying a bunch of new things in the space. Here are a few highlights.
- Built-in meeting notes
- Persistent chat with rich formatting
- Blurred background
- Virtual classroom with your coworkers
- Live captions
- Included with Microsoft subscription
1. Built-in meeting notes
Zoom is a video conferencing app—and that’s about it. What happens if you’re in the middle of an important meeting, but need a way to take some notes? You think you’d have to use Microsoft Word or another program, but did you know that Teams has its own meeting notes feature, too? Microsoft Teams is built around the idea that it will be the all in one tool you use for all collaboration: team chat, video calls, and even internal documentation.
Click Meeting notes, and a new tab for meeting minutes will be created in the current channel.
Notes get saved as part of the meeting itself, and can go anywhere with you, and will be saved for later or for sharing with your coworkers.
This is a quick way to ensure there’s a written record of the meeting in a place where everyone can access it, which is very slick.
Meeting Notes in Teams is a great way to capture every detail about your meetings on the platform. You can take and access notes before, during, and after a meeting in Teams. So, keep all your notes in one place while sharing them with your colleagues.
2. Persistent chat with rich formatting
Zoom chat is very simple. Microsoft Teams’ chat for meetings, on the other hand, has more formatting features than AIM.
We’re not sure if you have the multitasking skills to format text during a meeting, but it’s there if you want it. And this is just the beginning—there’s a large sticker collection and, for some reason, a meme creator. Imagine how much fun this can make your meetings!
Microsoft Teams also keeps a record of the chat from every meeting and posts all comments in the channel.
Have you ever lost track of helpful links and information during a Zoom meeting? With Teams, you can review the comments after the meeting, and any points made there can be found using search alongside the rest of your chats. It’s easy to see why this is useful.
3. Blur your background
Zoom backgrounds are, at this point, an important part of our collective human culture—the ultimate form of self-expression. With this best practice, you can have your meeting almost anywhere, and disguise whatever happens in the background around you. Naturally, Microsoft Teams offers custom backgrounds for meetings.
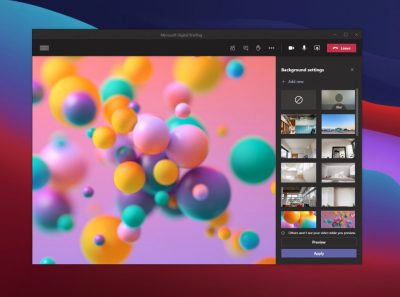
4. Pretend you’re in the same room as your coworkers
Zoom has two views that you can switch between. Speaker View and Gallery View: essentially, you can see the person talking right now or see everyone at once. Microsoft Teams adds another: Together Mode. Everyone on the call is shown as though they’re sitting next to each other in some kind of classroom, or sporting event like we’ve seen on TV with the NBA,MLB, NHS and NFL.
This is optional, and turning it on only changes things on your screen.
Is this useful? No. Will it make you feel slightly less alone during a year in which in-person interaction is rare? No. Is it somewhat amusing? Yes.
5. Live captions
Teams can detect what’s said in a meeting and present real-time captions. And, if you’ve turned on the new meeting experience, your captions will include speaker attribution—so you’ll see not only what’s being said, but who’s saying it.
Zoom offers a closed captioning feature, but someone has to manually type them out. Microsoft’s system recognizes speech automatically. Live captions can make your meeting more inclusive to participants who are deaf or hard-of-hearing, people with different levels of language proficiency, and participants in loud places by giving them another way to follow along.
6. There’s a good chance you’re already paying for it
Zoom is free, but the free version limits meetings to 40 minutes. Microsoft Teams’ free version has no such restrictions for video meetings.
There’s also a good chance you’re already paying for the full version. Microsoft Teams is included with every version of Microsoft 365 for business. This means that, if your company pays for a Microsoft Office subscription, you already have access to Teams. You should probably give it a chance and consider not paying for Zoom and/or Slack on top of it.
Features
- Group and private chat.
- Video calling, audio calling, and screen sharing.
- Schedule video calling.
- Thread messaging.
- Works seamlessly with any other Office app.
- Up to 250 people per video call.
- Over 270 integrations.
- Available in 53 languages.
Best for
- Microsoft-centric teams.
- Organizations that want to keep ideas organized and compartmentalized.
If you have any questions, please email us at support@sjtechies.com or call us at (856) 745-9990.