There’s plenty of free, effective anti-malware protection available. Just don’t let it push your browser around.
Although malware was once predicted to become extinct, it remains a constant threat. Thankfully, countless tools are available to help protect your PC against such security threats—including the popular (and free) anti-malware products on this list.
: AVG AntiVirus Free
AVG AntiVirus Free (Figure A) provides protection for your computer, your browser, and your mail client. Like many other free products, AVG AntiVirus Free tries to sell you a paid license, which includes an enhanced firewall, anti-spam protection, and a few other features.
Figure A
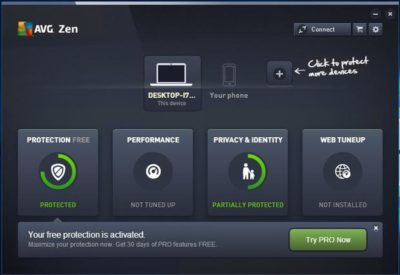
Although AVG AntiVirus Free seems to do a good job protecting systems against viruses, you have to be careful about the options you choose when installing and configuring this product. Otherwise, AVG will attempt to “hijack” your browser by installing AVG Web TuneUp, changing your search page, changing your new tab pages, and changing your home page.
2: Malwarebytes Anti-Malware Free
Malwarebytes Anti-Malware Free (Figure B) offers basic protection against malware. There are two main things I like about this app. First, unlike some of the other free anti-malware products, it doesn’t try to change your browser settings or install unwanted toolbars. Second, it has a clean and intuitive interface that doesn’t leave you guessing about what to do.
Figure B
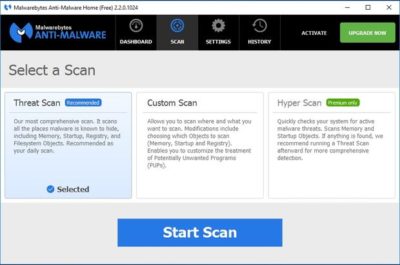
The disadvantage to using Malwarebytes Anti-Malware Free is that unlike the premium version, it does not support real-time protection. You can scan your PC for malware at any time, but you won’t be alerted to infections in real time unless you upgrade to the paid version.
3: Avast Free Antivirus 2016
Avast Free Antivirus 2016 (Figure C) is probably the most comprehensive antivirus tool on this list. It offers 12 components, including Rescue Disk, Browser Cleaner, Web Shield, and File Shield. The installer lets you choose which components to install.
Figure C
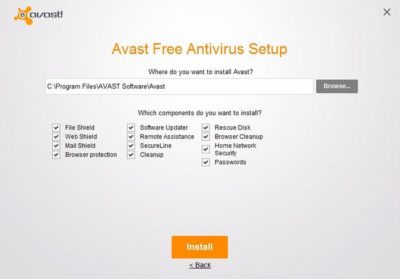
During the hour or so that I used Avast Free Antivirus, it did not attempt to take over my browser or engage in any other obnoxious behavior. The software does, however, prominently display a warning message during the installation process telling you in no uncertain terms that Avast Free Antivirus 2016 collects personal information. At least it gives you a way to opt out of this data collection.
4: Panda Free Antivirus
Panda Free Antivirus (Figure D) is another free anti-malware solution that requires a bit of caution during the installation process—otherwise, Panda will install a browser toolbar and change your home page and your default search provider.
Figure D
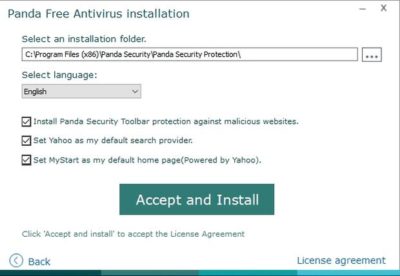
The free version of Panda Antivirus offers real-time protection against malware, but it does try to get you to upgrade to the paid version. That version, which Panda refers to as the Pro Edition, adds a firewall, Wi-Fi protection, and VIP support.
5: YAC
YAC (Figure E) stands for Yet Another Cleaner and—you guessed it—it’s yet another free tool for blocking threats and removing malware from an infected system. It offers a simple, easy-to-follow interface, and it doesn’t try to hijack your browser (which is a personal pet peeve, in case you hadn’t noticed). In fact, the software gives you a way to lock your browser settings so that your preferred home page, default browser, and default search engine can’t be changed without your consent.
Figure E
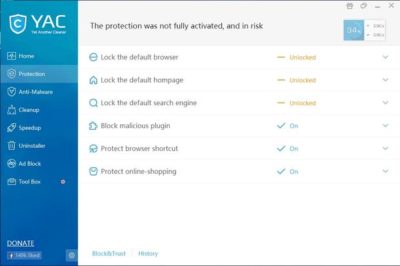
In addition to its basic anti-malware capabilities, YAC includes some nice extras, such as a tool for speeding up your computer, an uninstaller, and an ad blocker. The primary disadvantage to using YAC is that you have to upgrade to the paid version if you want to receive real-time protection. Otherwise, you’ll have to initiate anti-malware scans manually.
Have questions?
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.