Office 365 provides the productivity tools required by a modern enterprise workforce. This guide covers key details, including available applications, system requirements, and subscription options.

For just about any enterprise of any size, the productivity of its modern workforce revolves around the basic office suite of email, calendar, word processor, and spreadsheet. But as the enterprise workforce has become more mobile, the basic productivity toolset has had to adapt and change to match new requirements. This is why Microsoft updated Office 365 to be a mobile collaborative platform ready to get work done wherever and whenever it happens.
Microsoft Office 365 is the de facto productivity suite for many enterprises and it is the suite all the other competitors are measured against. So as a leader in information technology for your enterprise, it’s in your best interest to know everything there is to know about Office 365. To help you achieve that goal, TechRepublic compiled the most important details and related resources on Microsoft Office 365 into this “living” guide, which we’ll periodically update as new information becomes available.
Executive summary
What is it? Microsoft Office 365 provides users with the basic productivity applications necessary to get work done in the modern enterprise. It includes applications like Word, Excel, Outlook, PowerPoint, OneNote, and OneDrive, just to name a few.
Why does it matter? As the standard for productivity suites, competing products are generally measured against applications from the Office 365 suite.
Who does it affect? In the modern mobile-centric enterprise, Office 365 provides the tools used to get work done. This makes Office 365 important to just about every working individual.
When is it available? The latest version of Microsoft Office 365 is available right now. The current subscription includes Office 2016 applications.
How do you get it? Enterprises can purchase a subscription to Office 365 via the Microsoft website. Subscriptions range from $8/user/month to $35/user/month.
What is it?
Microsoft Office 365 is a subscription service that provides users with the basic productivity applications necessary to get work done in the modern enterprise. Productivity applications include, but are not limited to, a word processor, a spreadsheet, an email client, a calendar, and a presentation application.

As an example, a Business Premium subscription to Office 365 ($12.50 per person per month) includes these applications:
Word: This app sets the standard for word processors and is available with Office 365 for both Business and Premium. If users in your enterprise need to create documents, this is the tool they will use.
Excel: The spreadsheet has been the workhorse for basic data analysis since its invention back in the previous century. Excel is the current standard-bearer and comes with Office 365 for Business and Premium.
Outlook: Office 365’s solution for managing email and an appointment calendar is called Outlook. The app has been around for many years and its busy interface tends to be either loved or hated by users. It’s available with both the Business and Premium subscriptions.
PowerPoint: Communicating information to a group of individuals at a meeting often involves a presentation. Office 365’s PowerPoint allows users to create, display, and disseminate information in formats ranging from the basic slide to animation to video.
Publisher: Sometimes communicating information to a broader audience requires something more permanent and more formal than a presentation at a meeting. The Publisher app in Office 365 provides users with the tools they need to publish professional-looking newsletters, brochures, and booklets.
OneNote: As the workforce has become more mobile, the need to capture information on the go has become increasingly important. Applications like OneNote allow users to take notes on any device and then retrieve those notes from any other device. It’s your basic productivity cloud app.
OneDrive: The other basic and fundamental cloud-based application is storage. With each Office 365 Business subscription, Microsoft provides users with up to 1TB of cloud storage in the form of an application called OneDrive for Business.
SharePoint: A subscription to Office 365 Business Premium also provides an enterprise with a few applications for backend infrastructure management. SharePoint, for example, can be used to host intranet websites for the enterprise. It also can be used to host smaller sites designed for smaller teams or divisions. The permissions for these sites can be designated by the users themselves or by appointed administrators.
Exchange: Each Office 365 for Business subscription includes an Exchange Server, which handles all the email management duties. By default, each user is granted 50GB of storage for email. Maintenance of the Exchange Server is generally handled at the administrator level.
Collaboration tools: Along with the typical productivity applications, Office 365 includes many collaboration tools—like Delve, Skype, Yammer, and Sway. These tools allow users to communicate, brainstorm ideas, share documents, and have video meetings while on the go.
Power BI: One of the most powerful tools any enterprise can have, regardless of size, is reliable business intelligence gathering applications. Office 365 for Business, through its Power BI application, provides enterprises with a set of tools for collecting, sorting, and presenting business intelligence data.
Infrastructure: All Office 365 subscriptions include a reliability guarantee of 99.9% uptime. In addition, permissions for internal access control are handled by administrators designated by the enterprise using tools supplied by Active Directory. Each Office 365 subscription includes five layers of security and proactive monitoring to help safeguard your data.
System requirements
- CPU: 1GHz or faster
- Memory: 2GB RAM
- Hard drive: 3GB of available space (6GB for Mac)
- Display: 1280 X 800 screen resolution
- Operating system: PC-Windows 7, 8, or 10. Mac-Mac OS X 10.10
- Connectivity: Internet connection
Why does it matter?
Collaboration and communication are the key components of productivity in the modern enterprise, and productivity is the lifeblood of the enterprise. Microsoft Office 365 provides the tools necessary to bring collaboration and communication—and by extension, productivity—to each individual in an enterprise.
For many companies, Office 365 is the de facto standard for productivity software. The performance of all competing products is generally measured against applications from the Office 365 suite.
Who does it affect?
Just about every knowledge worker in every enterprise is required to have an email account and a calendar application. Beyond that, most individuals in an enterprise will need to use, at least once in a while, a word processor. And a significant number of individuals in an enterprise will also find themselves needing to use presentation software or a spreadsheet at some point in their career.
These are the productivity tools of any enterprise. These are the tools used to get work done. That means Office 365 is important to just about every working individual.
When is it available?
Microsoft Office 365 is available right now. The current subscription includes applications updated to the Office 2016 versions. Of course, the key to the subscription model is that each user will always be using the most current and most secure version of each application because each application is continuously updated.
How do you get it?
Enterprises with fewer than 300 users can purchase a subscription to Office 365 and download the appropriate applications via the Microsoft website. The Premium version costs $12.50 per user per month ($150/year). There are also versions of Office 365 available for individuals ($69.99/year) and households ($99.99/year).
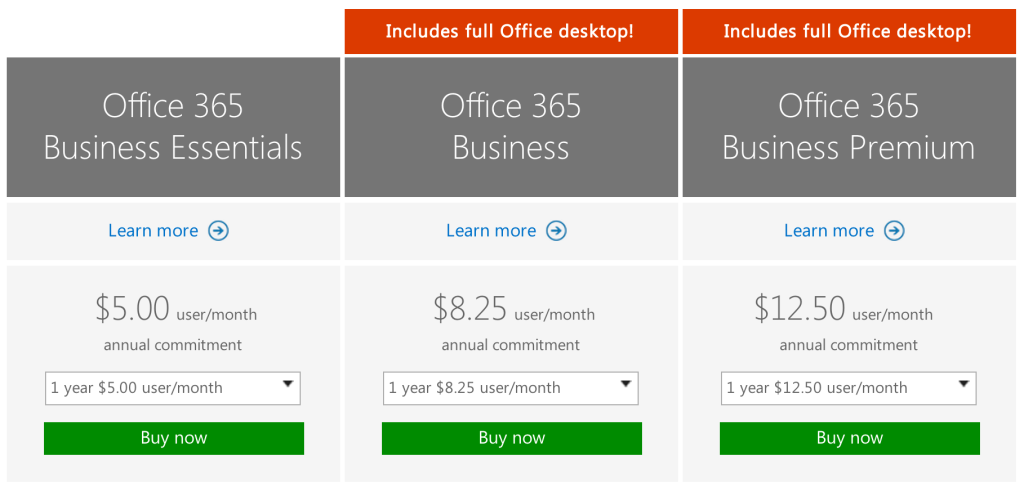
For large enterprises, unlimited user versions of Office 365 are available, ranging from $12 per person per month to $35 per person per month. Each subscription caters to a particular type of enterprise. More expensive enterprise versions of Office 365 add features like voicemail, compliance auditing, rights management, encryption, and Advanced Threat Protection.
Have questions?
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.