
What Is EU GDPR?
The EU GDPR is a law designed to protect and empower residents of the EU by guiding business usage of personal data. In essence, it is reshaping the way corporations handle personal data by controlling its collection, use, and storage. It will replace the regulations and frameworks of the existing 20-year-old directive (95/46/EC).
Who Is the GDPR Protecting and Empowering?
The data subject: This is any individual that can be directly or indirectly identified or uniquely singled out in a group of individuals, from any stored data.
What Is the GDPR Protecting?
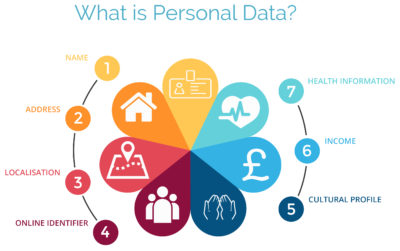
Personal data: This is any information relating to an individual, whether in reference to their private, professional, or public life. It includes things like names, photos, email addresses, location data, online identifiers, a person’s bank details, posts on social networking websites, medical information, work performance details, subscriptions, purchases, tax numbers, education or competencies, locations, usernames and passwords, hobbies, habits, lifestyles, or a person’s computer’s IP address.
Who Is the GDPR Regulating?
The data controller: This is the person who, alone or jointly with others, determines the purposes for, and means of, processing personal data. A data controller is not responsible for the act of processing (this falls to the data processor); they can be defined as the entity that determines motivation, condition, and means of processing.
Generally, the role of the controller is derived from the organization’s functional relation with the individual. That is, a business is the controller for the customer data it processes in relation to its sales, and an employer is the controller for the employee data they process in connection with the employment relationship.
Who Else Is the GDPR Regulating?

Data processors: This is the person who processes personal data on behalf of the controller. Typical processors are IT service providers (including hosting providers) and payroll administrators. The processor is required to process the personal data in accordance with the controller’s instructions and take adequate measures to protect the personal data. The GDPR does not allow data processors to use the personal data for other purposes beyond providing the services requested by the controller.
What Does the GDPR Consider “Processing?”
Processing refers to any operation or set of operations performed upon personal data, whether or not by automatic means—such as collection, recording, organization, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, blocking, erasure, or destruction. Processing must be fair and lawful, although transparency is significantly strengthened. The processor may not use the personal data for their own purposes.
What Rights Do the Data Subjects Have?
Under the GDPR, data subjects can request the following:
- To be informed about the data processing
- To consent to the processing of their personal data (opt in) or object to the processing of their personal data (opt out)
- To obtain their personal data in a structured and commonly used format in order to transfer that data, in certain circumstances, to another controller (data portability)
- To not be subject to fully automated data processing or profiling
- To know what data is processed (right of access)
- To correct where any data is incorrect
- To have data erased under certain circumstances, for example, where the retention period has lapsed or where consent for the processing has been withdrawn (referred to commonly as the “right to be forgotten”) and to register a complaint with the supervisory authority
Other Key Elements to Consider in Preparing for GDPR
We’re not done yet. There are four more important elements to consider with GDPR as you become ready.

1) Data Breach Notification
For controllers, GDPR requires that breach notice must be provided, where feasible, within 72 hours of becoming aware of a breach; processors need to provide notice to controllers without undue delay. Any data breaches must be documented.
2) Data Minimization
This requires the level and type of data being processed to be limited to the minimum amount of data necessary. This requires you to ensure that the purpose in which the data is agreed and the purpose in which the data was collected are materially similar. The processors should ensure that individuals’ privacy is considered at the outset of each new processing, product, service, or application, and only minimum amounts of data are processed for the specific purposes collected and processed.
3) Data Pseudonymization
The GDPR defines pseudonymization as “the processing of personal data in such a way that the data can no longer be attributed to a specific data subject without the use of additional information.” To pseudonymize data, the “additional information” must be “kept separately and subject to technical and organizational measures to ensure non-attribution to an identified or identifiable person.” In other words, it is a strategy designed to enhance protection and privacy for applicable identifying data.
Although similar, anonymization and pseudonymization are two distinct techniques that permit data controllers and processors to use de-identified data. The difference between the two techniques rests on whether the data can be re-identified.
4) Fair Processing of Personal Data
This requires the processing of personal data to be fair and lawful. Generally, only the level and type of data collected should be limited to the minimum amount of data necessary (see data minimization above). There are a number of methods in which the data may be processed, including: express consent (which may be withdrawn at any time), legitimate interest basis (the subject of which legitimacy may be challenged by the data subject), honoring obligations under the agreement with the data subject, or any other legal basis that may apply.
What We Can Do to Help
We know this information can be overwhelming, but taking the proper steps now will save you headaches later. SolarWinds provides products that can help you with getting ready. Our Risk Intelligence software is one of them, providing you with hard data on:
- A business’ quantified financial risk
- Personally identifiable information (PII)
- Protected health information
- Payment information located in storage
- Access permissions for sensitive data
Search your ‘data at rest’ for risk areas and start the data mapping you need to get ready for GDPR.