I realized handing over my entire life to one platform had its downsides.

I deleted Google from my life, and I can show you how to do it, too.
After being a devoted Googler for many years, I realized putting all my data on one platform had its downsides. A couple of factors in particular drove me to make a clean break.
Deleting Google for privacy and security
The appeal of escaping Google comes down to privacy. Google collects an alarming amount of data about you. It’s safe to say that if you’re not a paying customer then you’re the product being sold, and that’s Google’s business model.
Security goes hand-in-hand with that. I’m sure Google’s servers are closely guarded, but I still didn’t want all my data to be concentrated in one place.
To Google’s credit, the company gives you tools to opt out of the give-us-your-private-data-for-our-services game altogether. We cover the basics in these two articles:
- How to download your Google data so you can see what’s being recorded.
- How to delete your Google data to protect yourself.
Deleting Google for social impact
Another reason to get rid of Google is make your choice as a consumer for a healthier, more responsible media. As a working journalist, I’m acutely aware that Google and Facebook jointly dominate the media distribution and discovery landscape. With no strong competitors to Google Search in particular, Google’s algorithms hold unprecedented sway over the discourse in our society.
The importance of search discovery means that publishers and journalists must write stories to match the queries typed in by readers. That means coverage is guided by readers’ preconceived notions about a news event, not by objective reporting. That’s a deeply disturbing state of affairs for any democratic society.
Google outwardly seems as dedicated to responsible stewardship as one could hope, but it’s still concerning enough to merit supporting alternatives and competitors.
How my Google-free experiment started
When I decided to drop Google, I had just left a full-time job at a company that used Google mail and other apps. I stopped using all Google products while I freelanced. Note: If you’re an Android user, this is basically a no-go. Fortunately, I use a combination of Windows PCs, Macs, and iOS devices, so I wasn’t trapped.
Everyone uses Google differently, but I focused on forgoing the services that are core to the experience: Gmail, Docs, Drive, Calendar, Maps, and Search.
Dropping Gmail was easier than expected. I tried Yahoo! Mail, but there were too many ads for my taste. The web interface for Apple Mail at icloud.com was just adequate. I found Microsoft’s overhauled Outlook web interface (and truly excellent mobile app) was the best alternative.

Apple’s iWork for iCloud lets you use its productivity applications and share content across devices.
Instead of Docs, I tried Office 365 and iWork for iCloud. I liked them both better than Docs because I prefer native apps to web apps, and because I think both have more elegant designs—especially iCloud. Apple’s iWork for iCloud is similar to Docs in that it’s online-only, and designed for collaboration. It also has a mobile app. Office 365 will be pretty familiar to anyone who’s worked with Office’s desktop versions.
It was also pretty easy to kick Drive to the curb. Cloud storage competitors abound. I always preferred Dropbox to Drive anyway because I find that its OS X and Windows apps are better-integrated into the OS’s normal file browsing experience. Google Drive feels like it’s meant to be a place to store documents and back up files, not seamlessly augment your local storage—even though it does that in some ways.
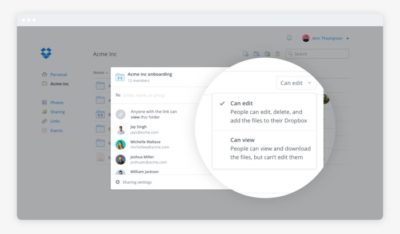
Dropbox’s file-sharing features are competitive and in some ways better than those in Google Docs.
Google Calendar has plenty of competition. This is a more personal choice, and people can get very attached—consider the furor when Microsoft shuttered Sunrise Calendar. On the other hand, it inspired us to find third-party alternative calendars, which could also replace Google Calendar.
What didn’t go well
I tried Apple Maps. I tried Waze. Google Maps is still the best.
I couldn’t quit everything Google offered so easily. Google Maps alternatives were a challenge. Your best bets are Waze or Apple Maps, but let’s be honest—they have nothing on Google Maps. Unlike Apple Maps, Waze has a web app, and powerful community-sourced data is its biggest selling point. But guess what? Google uses Waze’s data in Maps! So rather than gaining that feature, you’re just losing all the stuff Maps has that Waze doesn’t.
Google Search rules for a reason. The only two decent alternatives I found were Bing and DuckDuckGo.
Bing is as good or better than Google in many respects, but Google’s algorithms and semantic search win hands-down.
Bing is a strong competitor. Some features, like video search, are even better than what Google offers. But Bing’s algorithm and the semantic search show more cracks than Google’s do.
DuckDuckGo isn’t as full-featured, but it records no user data—that’s the primary selling point of the platform. Both search options were passable, but Google has nailed semantic search with a precision that no one else can touch.
Back in Google’s grasp
I lived Google-free for five months, compromises and all. Then I was hired at a new job that required me to use Google. I considered the experiment a success, to the point that I was dismayed to abandon it at the new gig.
Google has us in its grasp for good reason. Looking back at my life without it, I can honestly say some alternatives couldn’t compare. Your mileage may vary based on which services you value most. If you decide to delete Google from your life, too, let us know how it goes on our Facebook page.
Have questions?
Get answers from Microsofts Cloud Solutions Partner!
Call us at: 856-745-9990 or visit: https://southjerseytechies.net/
South Jersey Techies, LL C is a full Managed Web and Technology Services Company providing IT Services, Website Design Services, Server Support, Network Consulting, Internet Phones, Cloud Solutions Provider and much more. Contact for More Information.
To read this article in its entirety click here.